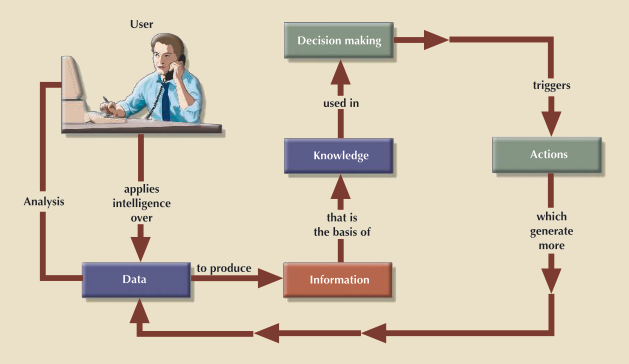
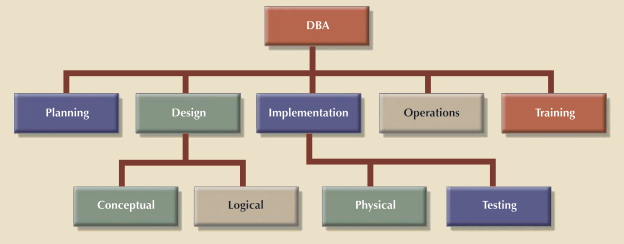
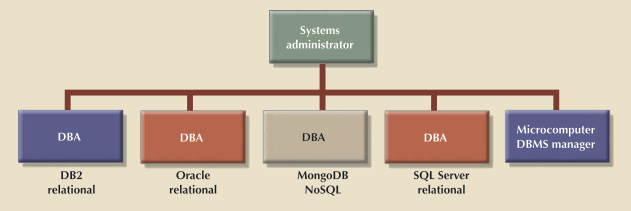
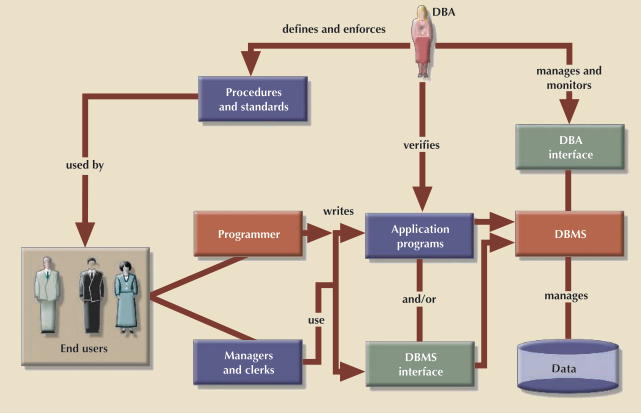
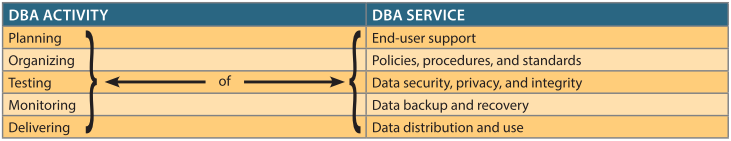
In today's information-driven environment, data is a valuable asset that requires careful management
Data is a valuable resource that can translate into information
If the information is accurate and timely, it can enhance the company's competitive position and generate wealthIn effect, an organization is subject to a data-information-decision cycle